
Protecting communication between machines is paramount in this tech-centric world. Businesses across all sectors rely on secure machine-to-machine (M2M) communication to optimize operations and stay ahead of competitors.
However, security measures must be taken with proper certificates and centralized SSH key management to protect data in this arena properly. In this blog post, we will explore how you can ensure M2M communication is secure through appropriate certificates and other key strategies and technologies.
Introducing The Importance Of Machine-To-Machine (M2M) Communication In Our Digital World
The need for seamless communication between devices has become increasingly important. This is where Machine-to-Machine (M2M) communication comes into play. By allowing smart devices to communicate with each other without human intervention, M2M enables businesses to automate processes, increase efficiency, and reduce costs.
This technology has already revolutionized industries such as healthcare and transportation, but its applications are limitless. As we continue to rely on interconnected devices, the importance of M2M communication will only continue to grow.
Examining The Concept Of Secure Communication Between Two Machines

Advancements in technology have streamlined information transfer through electronic devices. However, this progress also increases the risk of information breaches and cyber attacks. Secure communication between two machines, including the SSH key manager, is now a top priority. It refers to the ability of devices to exchange data without interception or unauthorized access.
Encryption techniques, security protocols, and SSH key managers protect the transmitted data. Secure communication remains evolving as hackers find new ways to bypass security measures. Nonetheless, its importance cannot be overstated, as it safeguards sensitive information.
Understanding What A Security Certificate Is And Its Role In M2M Communication
M2M communication has become increasingly important. However, with this rapid expansion of technology comes a need for security measures to protect the data being transmitted and received. That’s where security certificates come in.
A security certificate is a digital ID that verifies the identity of a device or entity participating in M2M communication. It ensures that data is encrypted and only accessible by the intended recipient.
Without security certificates, sensitive information could be compromised. Thus, understanding the role of security certificates in M2M communication is crucial for ensuring secure and reliable communication between devices.
Looking At Different Types Of Certificates Used For Securing M2M Communications
Securing machine-to-machine (M2M) communication is crucial. One way to ensure security is through certificates. Different types exist, each with unique features. For example, self-signed certificates are easy to create and cost-effective.
On the other hand, public key infrastructure (PKI) certificates provide a higher level of security and are issued by trusted authorities. Choosing the right certificate depends on trust, cost, and application. Implementing certificates carefully safeguards M2M communications and prevents breaches.
Analyzing Why It’s Important To Choose The Right Certificate For Your Specific Need
Choosing the right certificate can be crucial for obtaining a job, advancing your career, or ensuring employers recognize your skills. With the multitude of certificates available, it can be overwhelming to determine which one will suit your specific needs.
Researching your industry’s requirements, the certificate provider’s credibility and the cost and time commitment can all play a role in making the right decision. Investing in the right certificate can significantly impact your career trajectory and give you a sense of accomplishment and recognition.
Exploring The Process Of Obtaining A Security Certificate And How It Helps Ensure Secure Information Transmission
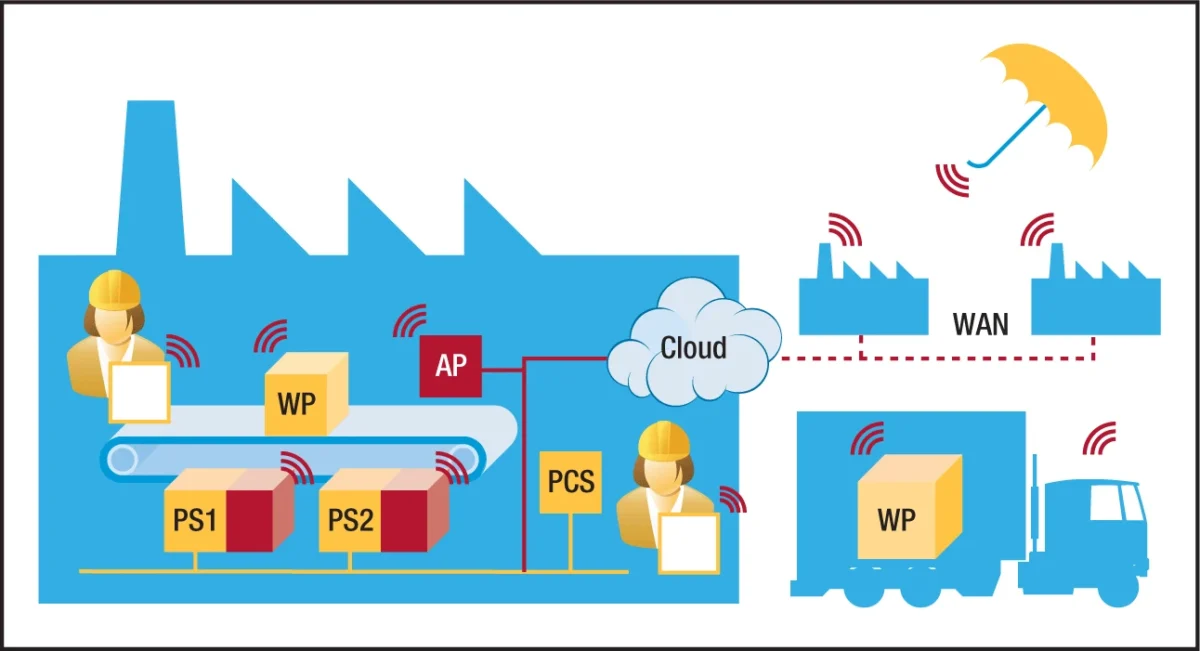
Our sensitive information is constantly transmitted over the internet. We rely heavily on secure networks to protect our data during banking transactions, personal emails, etc. Security certificates play a crucial role in ensuring encryption and security. Obtaining a certificate involves verifying the identity of the requester and preventing misuse.
With a security certificate, information exchanged between your browser and the web server is encrypted, keeping it secure from unauthorized access. In summary, security certificates are essential for secure information transmission in our digital world.
Final Thoughts
M2M Communication is vital, and ensuring secure data transmission between machines is crucial. Security certificates provide the necessary protection.
Understanding the right certificate for your application is essential. Obtaining a certificate may be complicated, but it safeguards your communication from threats. Implementing security certificates is crucial for reliable and conflict-free information transmission.
Selecting the right certificate requires effort, but the long-term benefits are worth it. Research security certificate options and choose one suitable for your application today to reap the rewards of M2M communications.








