Big Data, Because They Are So Important In Data Analysis
Chipping away at Big Data is a test that organizations of any size and modern area can't get away from today. In the mind-boggling...
The Benefits Of TypeScript: Why You Should Start Using It
If you’re a software developer, you’ve most likely heard of TypeScript and are wondering if it’s worth your time to learn and use. This...
5 Key Tools for A Modern Machinist
Having the right tools determines how fast and accurate you can finish a project. This statement is very true in a machinist workshop. Unfortunately,...
The Evolution of Twin Screw Extruder Technology
In the field of material processing and manufacturing, twin screw extruder technology has undergone a remarkable evolution, driving innovation and revolutionizing various industries. From...
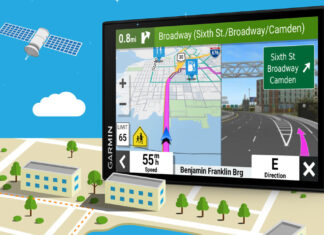
Demystifying Handheld Auto Navigation Equipment: What You Need to Know
Navigating the intricacies of modern technology can be as daunting as navigating an unknown terrain. Handheld auto navigation equipment, popularly known as GPS devices,...
How To Watch Over And Record User Activity On A PC?
There are many reasons to consider monitoring the activities and history on your PC. For example, if you have kids, it can be a...
How AI Technology Is Reshaping the Photo Editing Industry
Well, there is one unusual thing that we need to say here. Do you feel like you are living in the world of photography?...
How New Technologies are Helping in Students Learning?
Even though many teachers think of technology as nothing but a distraction in class, today’s students can’t even imagine going to school without Google....
Can Trendy Tech at Home Really Elevate Your Health and Lifestyle? Let’s Find Out!
In today's world, where technology touches every aspect of our lives, it's no surprise that innovative gadgets and apps are revolutionizing how we approach...
How to Restore Deleted Partition?
One of the ways to get the best out of your system’s primary storage drive is to partition it. Partitioning means breaking down the...